Gmail Is An Example Fo What Type Of Cloud Computing Service Model?

Cloud computing metaphor: the grouping of networked elements providing services need not be individually addressed or managed by users; instead, the entire provider-managed suite of hardware and software can be thought of as an baggy cloud.
Cloud computing [1] is the on-demand availability of computer system resource, especially data storage (cloud storage) and computing power, without directly active management past the user.[two] Big clouds often accept functions distributed over multiple locations, each location being a data center. Cloud computing relies on sharing of resource to accomplish coherence and typically using a "pay-as-you-go" model which can help in reducing majuscule expenses but may likewise atomic number 82 to unexpected operating expenses for unaware users.[3]
Value proposition [edit]
Advocates of public and hybrid clouds claim that cloud computing allows companies to avoid or minimize up-front It infrastructure costs. Proponents too claim that deject computing allows enterprises to get their applications upward and running faster, with improved manageability and less maintenance, and that it enables IT teams to more than rapidly arrange resource to meet fluctuating and unpredictable demand,[four] [5] [6] providing outburst computing adequacy: high computing power at certain periods of peak demand.[vii]
History [edit]
The term cloud was used to refer to platforms for distributed calculating as early as 1993, when Apple spin-off General Magic and AT&T used information technology in describing their (paired) Telescript and PersonaLink technologies.[8] In Wired'southward Apr 1994 feature "Bill and Andy's Fantabulous Adventure II", Andy Hertzfeld commented on Telescript, General Magic's distributed programming linguistic communication:
"The beauty of Telescript ... is that now, instead of just having a device to programme, we now have the entire Cloud out there, where a single program tin go and travel to many different sources of data and create a sort of a virtual service. No one had conceived that before. The example Jim White [the designer of Telescript, X.400 and ASN.1] uses now is a engagement-arranging service where a software agent goes to the blossom store and orders flowers then goes to the ticket store and gets the tickets for the show, and everything is communicated to both parties."[9]
Early history [edit]
During the 1960s, the initial concepts of time-sharing became popularized via RJE (Remote Job Entry);[ten] this terminology was more often than not associated with large vendors such as IBM and Dec. Total-fourth dimension-sharing solutions were bachelor by the early 1970s on such platforms equally Multics (on GE hardware), Cambridge CTSS, and the earliest UNIX ports (on DEC hardware). Even so, the "data center" model where users submitted jobs to operators to run on IBM's mainframes was overwhelmingly predominant.
In the 1990s, telecommunication companies, who previously offered primarily defended point-to-point data circuits, began offering virtual private network (VPN) services with comparable quality of service, but at a lower cost. Past switching traffic as they saw fit to remainder server use, they could use overall network bandwidth more than effectively.[ citation needed ] They began to utilise the cloud symbol to denote the demarcation betoken betwixt what the provider was responsible for and what users were responsible for. Cloud computing extended this boundary to cover all servers also as the network infrastructure.[eleven] As computers became more diffused, scientists and technologists explored ways to make big-scale calculating ability available to more than users through time-sharing.[ citation needed ] They experimented with algorithms to optimize the infrastructure, platform, and applications to prioritize CPUs and increase efficiency for stop users.[12]
The use of the cloud metaphor for virtualized services dates at least to General Magic in 1994, where it was used to describe the universe of "places" that mobile agents in the Telescript surroundings could go. Every bit described by Andy Hertzfeld:
"The beauty of Telescript," says Andy, "is that now, instead of merely having a device to program, we now have the unabridged Cloud out there, where a single program can go and travel to many unlike sources of information and create a sort of a virtual service."[13]
The use of the deject metaphor is credited to General Magic communications employee David Hoffman, based on long-standing employ in networking and telecom. In improver to use by Full general Magic itself, it was also used in promoting AT&T'southward associated PersonaLink Services.[14]
2000s [edit]
In July 2002, Amazon created subsidiary Amazon Web Services, with the goal to "enable developers to build innovative and entrepreneurial applications on their own." In March 2006 Amazon introduced its Uncomplicated Storage Service (S3), followed by Elastic Compute Cloud (EC2) in August of the same year.[15] [sixteen] These products pioneered the usage of server virtualization to deliver IaaS at a cheaper and on-need pricing basis.
In April 2008, Google released the beta version of Google App Engine.[17] The App Engine was a PaaS (one of the first of its kind) which provided fully maintained infrastructure and a deployment platform for users to create web applications using common languages/technologies such as Python, Node.js and PHP. The goal was to eliminate the demand for some authoritative tasks typical of an IaaS model, while creating a platform where users could easily deploy such applications and scale them to demand.[xviii]
In early 2008, NASA's Nebula,[nineteen] enhanced in the RESERVOIR European Commission-funded projection, became the kickoff open-source software for deploying private and hybrid clouds, and for the federation of clouds.[20]
By mid-2008, Gartner saw an opportunity for cloud calculating "to shape the relationship amid consumers of IT services, those who use Information technology services and those who sell them"[21] and observed that "organizations are switching from company-endemic hardware and software assets to per-utilise service-based models" and so that the "projected shift to computing ... will effect in dramatic growth in IT products in some areas and significant reductions in other areas."[22]
In 2008, the U.S. National Science Foundation began the Cluster Exploratory program to fund academic research using Google-IBM cluster engineering to analyze massive amounts of data.[23]
In 2009, the authorities of French republic appear Project Andromède to create a "sovereign cloud" or national cloud computing, with the government to spend €285 meg.[24] [25] The initiative failed desperately and Cloudwatt was shut down on 1 February 2020.[26] [27]
2010s [edit]
In February 2010, Microsoft released Microsoft Azure, which was appear in October 2008.[28]
In July 2010, Rackspace Hosting and NASA jointly launched an open-source deject-software initiative known every bit OpenStack. The OpenStack projection intended to help organizations offering cloud-computing services running on standard hardware. The early code came from NASA's Nebula platform as well every bit from Rackspace's Cloud Files platform. As an open-source offer and forth with other open-source solutions such as CloudStack, Ganeti, and OpenNebula, it has attracted attention by several key communities. Several studies aim at comparison these open source offerings based on a set of criteria.[29] [30] [31] [32] [33] [34] [35]
On March 1, 2011, IBM announced the IBM SmartCloud framework to support Smarter Planet.[36] Amidst the diverse components of the Smarter Computing foundation, deject computing is a critical part. On June 7, 2012, Oracle announced the Oracle Deject.[37] This deject offer is poised to exist the first to provide users with access to an integrated set of IT solutions, including the Applications (SaaS), Platform (PaaS), and Infrastructure (IaaS) layers.[38] [39] [40]
In May 2012, Google Compute Engine was released in preview, before being rolled out into General Availability in December 2013.[41]
In 2019, Linux was the most common Os used on Microsoft Azure.[42] In December 2019, Amazon appear AWS Outposts, which is a fully managed service that extends AWS infrastructure, AWS services, APIs, and tools to nigh whatever client datacenter, co-location infinite, or on-bounds facility for a truly consequent hybrid experience[43]
Like concepts [edit]
The goal of cloud computing is to allow users to have benefit from all of these technologies, without the need for deep noesis about or expertise with each one of them. The deject aims to cutting costs and helps the users focus on their core business instead of existence impeded by It obstacles.[44] The main enabling technology for cloud computing is virtualization. Virtualization software separates a concrete calculating device into one or more than "virtual" devices, each of which tin can be easily used and managed to perform computing tasks. With operating system–level virtualization essentially creating a scalable system of multiple contained computing devices, idle calculating resources can be allocated and used more efficiently. Virtualization provides the agility required to speed upwards IT operations and reduces cost by increasing infrastructure utilization. Autonomic computing automates the process through which the user can provision resources on-demand. By minimizing user involvement, automation speeds up the process, reduces labor costs and reduces the possibility of homo errors.[44]
Cloud calculating uses concepts from utility computing to provide metrics for the services used. Cloud computing attempts to address QoS (quality of service) and reliability problems of other filigree computing models.[44]
Cloud computing shares characteristics with:
- Client–server model—Client–server computing refers broadly to any distributed application that distinguishes between service providers (servers) and service requestors (clients).[45]
- Computer bureau—A service agency providing reckoner services, particularly from the 1960s to 1980s.
- Grid computing—A form of distributed and parallel calculating, whereby a 'super and virtual computer' is composed of a cluster of networked, loosely coupled computers acting in concert to perform very big tasks.
- Fog computing—Distributed computing prototype that provides data, compute, storage and application services closer to the client or near-user edge devices, such as network routers. Furthermore, fog computing handles data at the network level, on smart devices and on the end-user client-side (e.chiliad. mobile devices), instead of sending data to a remote location for processing.
- Utility computing—The "packaging of computing resources, such equally computation and storage, as a metered service similar to a traditional public utility, such as electricity."[46] [47]
- Peer-to-peer—A distributed architecture without the need for key coordination. Participants are both suppliers and consumers of resource (in contrast to the traditional customer-server model).
- Cloud sandbox—A live, isolated computer environment in which a programme, code or file tin can run without affecting the application in which it runs.
Characteristics [edit]
Cloud computing exhibits the following key characteristics:
- Agility for organizations may be improved, every bit cloud computing may increase users' flexibility with re-provisioning, adding, or expanding technological infrastructure resources.
- Cost reductions are claimed past cloud providers. A public-cloud delivery model converts capital expenditures (e.thousand., buying servers) to operational expenditure.[48] This purportedly lowers barriers to entry, as infrastructure is typically provided past a third party and need not be purchased for quondam or infrequent intensive computing tasks. Pricing on a utility calculating basis is "fine-grained", with usage-based billing options. As well, less in-house IT skills are required for implementation of projects that apply cloud calculating.[49] The east-Financial project's state-of-the-art repository[fifty] contains several manufactures looking into toll aspects in more detail, nigh of them terminal that costs savings depend on the type of activities supported and the blazon of infrastructure available in-house.
- Device and location independence[51] enable users to admission systems using a web browser regardless of their location or what device they use (e.g., PC, mobile telephone). Equally infrastructure is off-site (typically provided past a third-political party) and accessed via the Internet, users can connect to it from anywhere.[49]
- Maintenance of cloud environment is easier because the data is hosted on an outside server maintained by a provider without the demand to invest in data center hardware. IT maintenance of deject computing is managed and updated by the deject provider'due south IT maintenance team that reduces cloud computing costs compared with the on-premises information centers.
- Multitenancy enables sharing of resources and costs across a large pool of users thus allowing for:
- centralization of infrastructure in locations with lower costs (such as real estate, electricity, etc.)
- peak-load chapters increases (users need not engineer and pay for the resource and equipment to run into their highest possible load-levels)
- utilisation and efficiency improvements for systems that are often but 10–20% utilised.[52] [53]
- Performance is monitored past IT experts from the service provider, and consistent and loosely coupled architectures are constructed using web services as the organization interface.[49] [54]
- Productivity may be increased when multiple users tin work on the same data simultaneously, rather than waiting for it to be saved and emailed. Time may be saved as information does non need to be re-entered when fields are matched, nor practice users need to install application software upgrades to their figurer.
- Availability improves with the apply of multiple redundant sites, which makes well-designed cloud computing suitable for business continuity and disaster recovery.[55]
- Scalability and elasticity via dynamic ("on-demand") provisioning of resources on a fine-grained, self-service basis in near existent-time[56] [57] (Note, the VM startup time varies by VM type, location, OS and cloud providers[56]), without users having to engineer for elevation loads.[58] [59] [sixty] This gives the power to scale up when the usage need increases or downwardly if resources are non being used.[61] The time-efficient do good of cloud scalability as well means faster time to market, more business flexibility, and adaptability, equally adding new resources doesn't take as much time equally it used to.[62] Emerging approaches for managing elasticity include the use of machine learning techniques to propose efficient elasticity models.[63]
- Security can improve due to centralization of data, increased security-focused resources, etc., but concerns tin can persist almost loss of control over certain sensitive data, and the lack of security for stored kernels. Security is frequently as good as or better than other traditional systems, in role considering service providers are able to devote resources to solving security bug that many customers cannot afford to tackle or which they lack the technical skills to accost.[64] However, the complication of security is greatly increased when data is distributed over a wider surface area or over a greater number of devices, as well as in multi-tenant systems shared past unrelated users. In addition, user admission to security inspect logs may be difficult or impossible. Private cloud installations are in office motivated by users' desire to retain command over the infrastructure and avoid losing command of information security.
The National Institute of Standards and Engineering science's definition of cloud computing identifies "five essential characteristics":
On-demand self-service. A consumer can unilaterally provision computing capabilities, such as server time and network storage, equally needed automatically without requiring homo interaction with each service provider.
Broad network admission. Capabilities are available over the network and accessed through standard mechanisms that promote apply by heterogeneous thin or thick client platforms (due east.g., mobile phones, tablets, laptops, and workstations).
Resource pooling. The provider'southward calculating resources are pooled to serve multiple consumers using a multi-tenant model, with unlike physical and virtual resources dynamically assigned and reassigned according to consumer demand.
Rapid elasticity. Capabilities can be elastically provisioned and released, in some cases automatically, to calibration rapidly outward and inward commensurate with need. To the consumer, the capabilities available for provisioning often appear unlimited and can be appropriated in any quantity at whatsoever time.
Measured service. Deject systems automatically control and optimize resources use by leveraging a metering capability at some level of brainchild advisable to the type of service (e.thou., storage, processing, bandwidth, and active user accounts). Resource usage can exist monitored, controlled, and reported, providing transparency for both the provider and consumer of the utilized service.
—National Institute of Standards and Technology[65]
Service models [edit]

Cloud calculating service models arranged as layers in a stack
Though service-oriented architecture advocates "Everything every bit a service" (with the acronyms EaaS or XaaS,[66] or simply aas), cloud-calculating providers offer their "services" according to unlike models, of which the three standard models per NIST are Infrastructure equally a Service (IaaS), Platform as a Service (PaaS), and Software every bit a Service (SaaS).[65] These models offer increasing abstraction; they are thus often portrayed every bit layers in a stack: infrastructure-, platform- and software-as-a-service, but these demand not exist related. For example, one tin can provide SaaS implemented on physical machines (blank metal), without using underlying PaaS or IaaS layers, and conversely ane can run a plan on IaaS and admission it directly, without wrapping it as SaaS.
Infrastructure every bit a service (IaaS) [edit]
"Infrastructure as a service" (IaaS) refers to online services that provide loftier-level APIs used to abstract various low-level details of underlying network infrastructure like physical computing resources, location, data partitioning, scaling, security, fill-in, etc. A hypervisor runs the virtual machines equally guests. Pools of hypervisors within the deject operational organisation can support large numbers of virtual machines and the ability to calibration services upwards and downwards co-ordinate to customers' varying requirements. Linux containers run in isolated partitions of a unmarried Linux kernel running straight on the physical hardware. Linux cgroups and namespaces are the underlying Linux kernel technologies used to isolate, secure and manage the containers. Containerisation offers higher performance than virtualization because at that place is no hypervisor overhead. IaaS clouds ofttimes offer boosted resource such as a virtual-machine disk-image library, raw block storage, file or object storage, firewalls, load balancers, IP addresses, virtual local area networks (VLANs), and software bundles.[67]
The NIST's definition of cloud calculating describes IaaS as "where the consumer is able to deploy and run capricious software, which can include operating systems and applications. The consumer does not manage or control the underlying deject infrastructure just has command over operating systems, storage, and deployed applications; and possibly limited control of select networking components (east.1000., host firewalls)."[65]
IaaS-deject providers supply these resources on-demand from their big pools of equipment installed in information centers. For wide-expanse connectivity, customers can use either the Internet or carrier clouds (dedicated virtual private networks). To deploy their applications, cloud users install operating-system images and their application software on the cloud infrastructure. In this model, the cloud user patches and maintains the operating systems and the application software. Cloud providers typically bill IaaS services on a utility computing ground: toll reflects the amount of resource allocated and consumed.[ citation needed ]
Platform as a service (PaaS) [edit]
The NIST'due south definition of deject computing defines Platform every bit a Service as:[65]
The capability provided to the consumer is to deploy onto the deject infrastructure consumer-created or caused applications created using programming languages, libraries, services, and tools supported past the provider. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, or storage, only has command over the deployed applications and possibly configuration settings for the application-hosting environment.
PaaS vendors offer a development surroundings to awarding developers. The provider typically develops toolkit and standards for development and channels for distribution and payment. In the PaaS models, cloud providers evangelize a calculating platform, typically including operating organization, programming-language execution environment, database, and spider web server. Awarding developers develop and run their software on a deject platform instead of direct buying and managing the underlying hardware and software layers. With some PaaS, the underlying reckoner and storage resources scale automatically to match application demand so that the cloud user does non have to allocate resources manually.[68] [ need quotation to verify ]
Some integration and data management providers too use specialized applications of PaaS as delivery models for data. Examples include iPaaS (Integration Platform as a Service) and dPaaS (Data Platform as a Service). iPaaS enables customers to develop, execute and govern integration flows.[69] Under the iPaaS integration model, customers drive the development and deployment of integrations without installing or managing any hardware or middleware.[lxx] dPaaS delivers integration—and data-direction—products as a fully managed service.[71] Under the dPaaS model, the PaaS provider, not the client, manages the evolution and execution of programs past edifice information applications for the customer. dPaaS users admission data through data-visualization tools.[72]
Software as a service (SaaS) [edit]
The NIST's definition of deject computing defines Software as a Service every bit:[65]
The capability provided to the consumer is to use the provider's applications running on a cloud infrastructure. The applications are accessible from various client devices through either a thin client interface, such as a web browser (eastward.thou., web-based electronic mail), or a program interface. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage, or fifty-fifty individual awarding capabilities, with the possible exception of express user-specific awarding configuration settings.
In the software as a service (SaaS) model, users gain access to application software and databases. Cloud providers manage the infrastructure and platforms that run the applications. SaaS is sometimes referred to equally "on-demand software" and is ordinarily priced on a pay-per-use basis or using a subscription fee.[73] In the SaaS model, cloud providers install and operate application software in the cloud and cloud users access the software from deject clients. Cloud users do non manage the cloud infrastructure and platform where the application runs. This eliminates the need to install and run the awarding on the cloud user's own computers, which simplifies maintenance and support. Deject applications differ from other applications in their scalability—which tin can exist achieved by cloning tasks onto multiple virtual machines at run-time to meet irresolute work demand.[74] Load balancers distribute the work over the set of virtual machines. This process is transparent to the cloud user, who sees but a single access-point. To accommodate a large number of cloud users, cloud applications can be multitenant, pregnant that any machine may serve more than i deject-user organisation.
The pricing model for SaaS applications is typically a monthly or yearly flat fee per user,[75] so prices become scalable and adjustable if users are added or removed at whatsoever point. It may too be free.[76] Proponents claim that SaaS gives a concern the potential to reduce IT operational costs past outsourcing hardware and software maintenance and support to the cloud provider. This enables the business to reallocate IT operations costs away from hardware/software spending and from personnel expenses, towards meeting other goals. In addition, with applications hosted centrally, updates can be released without the need for users to install new software. I drawback of SaaS comes with storing the users' data on the cloud provider's server. As a issue,[ citation needed ] there could be unauthorized access to the data.[77] Examples of applications offered as SaaS are games and productivity software like Google Docs and Word Online. SaaS applications may be integrated with cloud storage or File hosting services, which is the case with Google Docs being integrated with Google Drive and Word Online being integrated with Onedrive.[ citation needed ]
Mobile "backend" as a service (MBaaS) [edit]
In the mobile "backend" as a service (m) model, too known as backend as a service (BaaS), web app and mobile app developers are provided with a way to link their applications to cloud storage and cloud computing services with application programming interfaces (APIs) exposed to their applications and custom software evolution kits (SDKs). Services include user management, push button notifications, integration with social networking services[78] and more. This is a relatively recent model in cloud computing,[79] with most BaaS startups dating from 2011 or later on[80] [81] [82] only trends indicate that these services are gaining significant mainstream traction with enterprise consumers.[83]
Serverless computing or Function-equally-a-Service (FaaS) [edit]
Serverless computing is a cloud calculating code execution model in which the deject provider fully manages starting and stopping virtual machines as necessary to serve requests, and requests are billed by an abstract measure of the resource required to satisfy the request, rather than per virtual machine, per hour.[84] Despite the name, it does non actually involve running code without servers.[84] Serverless computing is and so named because the business or person that owns the system does non accept to purchase, rent or provide servers or virtual machines for the back-end code to run on.
Function as a service (FaaS) is a service-hosted remote process phone call that leverages serverless computing to enable the deployment of private functions in the cloud that run in response to events.[85] FaaS is considered by some to come up under the umbrella of serverless calculating, while some others use the terms interchangeably.[86]
Deployment models [edit]

Private cloud [edit]
Private cloud is cloud infrastructure operated solely for a single organisation, whether managed internally or by a third political party, and hosted either internally or externally.[65] Undertaking a private cloud projection requires pregnant engagement to virtualize the business organisation environment, and requires the organization to reevaluate decisions about existing resource. Information technology can better business, but every step in the project raises security issues that must be addressed to prevent serious vulnerabilities. Self-run data centers[87] are generally capital intensive. They have a significant physical footprint, requiring allocations of infinite, hardware, and environmental controls. These assets take to be refreshed periodically, resulting in additional capital expenditures. They accept attracted criticism because users "still have to buy, build, and manage them" and thus do not benefit from less easily-on direction,[88] essentially "[defective] the economical model that makes cloud computing such an intriguing concept".[89] [90]
Public cloud [edit]
Deject services are considered "public" when they are delivered over the public Internet, and they may exist offered equally a paid subscription, or free of accuse.[91] Architecturally, at that place are few differences between public- and private-cloud services, but security concerns increase substantially when services (applications, storage, and other resources) are shared by multiple customers. Most public-cloud providers offer direct-connectedness services that allow customers to deeply link their legacy data centers to their cloud-resident applications.[49] [92]
Several factors similar the functionality of the solutions, cost, integrational and organizational aspects besides equally rubber & security are influencing the decision of enterprises and organizations to choose a public cloud or on-premises solution.[93]
Hybrid cloud [edit]
Hybrid deject is a composition of a public cloud and a private environment, such as a private cloud or on-bounds resources,[94] [95] that remain distinct entities but are bound together, offer the benefits of multiple deployment models. Hybrid cloud can also mean the ability to connect collocation, managed and/or dedicated services with deject resources.[65] Gartner defines a hybrid cloud service as a deject calculating service that is equanimous of some combination of private, public and community cloud services, from different service providers.[96] A hybrid cloud service crosses isolation and provider boundaries then that it can't be but put in one category of private, public, or community cloud service. It allows one to extend either the capacity or the capability of a cloud service, past assemblage, integration or customization with some other cloud service.
Varied use cases for hybrid cloud composition be. For example, an arrangement may store sensitive customer data in house on a private cloud awarding, but interconnect that awarding to a business intelligence application provided on a public cloud as a software service.[97] This example of hybrid cloud extends the capabilities of the enterprise to deliver a specific business organisation service through the improver of externally available public deject services. Hybrid cloud adoption depends on a number of factors such as data security and compliance requirements, level of control needed over data, and the applications an system uses.[98]
Some other example of hybrid cloud is i where IT organizations use public deject computing resource to meet temporary chapters needs that tin can non exist met past the individual deject.[99] This capability enables hybrid clouds to use cloud bursting for scaling across clouds.[65] Cloud bursting is an application deployment model in which an application runs in a individual cloud or information center and "bursts" to a public cloud when the demand for computing capacity increases. A master advantage of cloud bursting and a hybrid deject model is that an system pays for extra compute resources only when they are needed.[100] Deject bursting enables information centers to create an in-house Information technology infrastructure that supports boilerplate workloads, and utilize cloud resources from public or private clouds, during spikes in processing demands.[101] The specialized model of hybrid cloud, which is built atop heterogeneous hardware, is called "Cross-platform Hybrid Cloud". A cross-platform hybrid deject is ordinarily powered by dissimilar CPU architectures, for example, x86-64 and ARM, underneath. Users can transparently deploy and scale applications without knowledge of the cloud's hardware diversity.[102] This kind of deject emerges from the ascension of ARM-based organisation-on-bit for server-class computing.
Hybrid cloud infrastructure essentially serves to eliminate limitations inherent to the multi-access relay characteristics of individual deject networking. The advantages include enhanced runtime flexibility and adaptive memory processing unique to virtualized interface models.[103]
Others [edit]
[edit]
Community cloud shares infrastructure between several organizations from a specific community with mutual concerns (security, compliance, jurisdiction, etc.), whether managed internally or past a 3rd-party, and either hosted internally or externally. The costs are spread over fewer users than a public cloud (simply more than a private cloud), so but some of the cost savings potential of cloud computing are realized.[65]
Distributed cloud [edit]
A deject calculating platform can be assembled from a distributed set of machines in different locations, connected to a single network or hub service. It is possible to distinguish between ii types of distributed clouds: public-resource computing and volunteer deject.
- Public-resource computing—This blazon of distributed cloud results from an expansive definition of cloud computing, because they are more akin to distributed calculating than cloud computing. Notwithstanding, it is considered a sub-grade of cloud calculating.
- Volunteer cloud—Volunteer cloud computing is characterized every bit the intersection of public-resource computing and cloud computing, where a deject computing infrastructure is congenital using volunteered resources. Many challenges arise from this type of infrastructure, because of the volatility of the resources used to build it and the dynamic environment it operates in. It can also be called peer-to-peer clouds, or advert-hoc clouds. An interesting try in such management is Cloud@Dwelling house, information technology aims to implement a cloud computing infrastructure using volunteered resource providing a business-model to incentivize contributions through financial restitution.[104]
Multicloud [edit]
Multicloud is the utilize of multiple deject computing services in a single heterogeneous architecture to reduce reliance on single vendors, increase flexibility through choice, mitigate against disasters, etc. It differs from hybrid deject in that it refers to multiple cloud services, rather than multiple deployment modes (public, private, legacy).[105] [106] [107]
Poly cloud [edit]
Poly cloud refers to the employ of multiple public clouds for the purpose of leveraging specific services that each provider offers. It differs from Multi cloud in that it is not designed to increase flexibility or mitigate confronting failures just is rather used to allow an arrangement to attain more that could be done with a unmarried provider.[108]
Big data cloud [edit]
The issues of transferring large amounts of data to the cloud likewise as information security once the data is in the cloud initially hampered adoption of cloud for big data, but now that much information originates in the cloud and with the appearance of blank-metal servers, the cloud has become[109] a solution for utilize cases including business analytics and geospatial analysis.[110]
HPC cloud [edit]
HPC cloud refers to the use of deject calculating services and infrastructure to execute high-operation computing (HPC) applications.[111] These applications consume considerable amount of computing power and memory and are traditionally executed on clusters of computers. In 2016 a handful of companies, including R-HPC, Amazon Web Services, Univa, Silicon Graphics International, Sabalcore, Gomput, and Penguin Computing offered a loftier performance computing cloud. The Penguin On Demand (POD) cloud was one of the outset non-virtualized remote HPC services offered on a pay-equally-y'all-get footing.[112] [113] Penguin Computing launched its HPC deject in 2016 as alternative to Amazon'due south EC2 Elastic Compute Cloud, which uses virtualized computing nodes.[114] [115]
Architecture [edit]
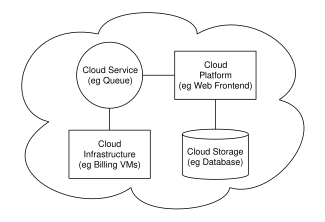
Cloud computing sample architecture
Deject compages,[116] the systems architecture of the software systems involved in the delivery of cloud calculating, typically involves multiple cloud components communicating with each other over a loose coupling machinery such as a messaging queue. Elastic provision implies intelligence in the use of tight or loose coupling as applied to mechanisms such as these and others.
Cloud technology [edit]
Cloud engineering is the application of engineering disciplines of cloud computing. It brings a systematic approach to the high-level concerns of commercialization, standardization and governance in conceiving, developing, operating and maintaining deject computing systems. It is a multidisciplinary method encompassing contributions from diverse areas such every bit systems, software, spider web, performance, data engineering engineering, security, platform, risk, and quality engineering.
Security and privacy [edit]

Cloud suppliers security and privacy agreements must be alligned to the need(s) requirements
Cloud computing poses privacy concerns because the service provider can access the information that is in the cloud at whatever time. Information technology could accidentally or deliberately alter or delete data.[117] Many deject providers can share information with 3rd parties if necessary for purposes of law and order without a warrant. That is permitted in their privacy policies, which users must agree to before they start using cloud services. Solutions to privacy include policy and legislation besides as end-users' choices for how data is stored.[117] Users tin encrypt data that is candy or stored within the cloud to prevent unauthorized access.[118] [117] Identity management systems can likewise provide applied solutions to privacy concerns in cloud computing. These systems distinguish between authorized and unauthorized users and determine the amount of data that is attainable to each entity.[119] The systems work by creating and describing identities, recording activities, and getting rid of unused identities.
According to the Cloud Security Alliance, the top three threats in the cloud are Insecure Interfaces and APIs, Data Loss & Leakage, and Hardware Failure—which accounted for 29%, 25% and 10% of all cloud security outages respectively. Together, these form shared engineering vulnerabilities. In a deject provider platform existence shared by different users, there may be a possibility that information belonging to dissimilar customers resides on the same information server. Additionally, Eugene Schultz, chief technology officer at Emagined Security, said that hackers are spending substantial fourth dimension and effort looking for ways to penetrate the deject. "There are some real Achilles' heels in the cloud infrastructure that are making large holes for the bad guys to get into". Considering data from hundreds or thousands of companies can be stored on large cloud servers, hackers can theoretically gain control of huge stores of information through a single attack—a process he called "hyperjacking". Some examples of this include the Dropbox security breach, and iCloud 2014 leak.[120] Dropbox had been breached in Oct 2014, having over vii meg of its users passwords stolen by hackers in an effort to get monetary value from it by Bitcoins (BTC). Past having these passwords, they are able to read private data as well as take this data exist indexed past search engines (making the data public).[120]
In that location is the problem of legal buying of the data (If a user stores some data in the cloud, tin the cloud provider profit from it?). Many Terms of Service agreements are silent on the question of ownership.[121] Physical control of the computer equipment (private deject) is more secure than having the equipment off-site and under someone else'due south control (public cloud). This delivers great incentive to public cloud calculating service providers to prioritize building and maintaining stiff management of secure services.[122] Some small businesses that don't have expertise in It security could find that it's more secure for them to use a public cloud. There is the risk that cease users do not sympathise the bug involved when signing on to a cloud service (persons sometimes don't read the many pages of the terms of service understanding, and just click "Accept" without reading). This is important at present that cloud computing is common and required for some services to work, for example for an intelligent personal banana (Apple'southward Siri or Google Assistant). Fundamentally, private cloud is seen as more than secure with college levels of command for the owner, however public cloud is seen to be more than flexible and requires less time and money investment from the user.[123]
Limitations and disadvantages [edit]
According to Bruce Schneier, "The downside is that you will take limited customization options. Cloud computing is cheaper because of economic science of scale, and—like whatever outsourced task—you tend to get what you want. A eating house with a limited menu is cheaper than a personal chef who can cook anything y'all want. Fewer options at a much cheaper price: information technology's a feature, non a issues." He also suggests that "the cloud provider might non meet your legal needs" and that businesses need to counterbalance the benefits of deject computing against the risks.[124] In cloud calculating, the control of the back end infrastructure is limited to the deject vendor only. Cloud providers often make up one's mind on the direction policies, which moderates what the deject users are able to do with their deployment.[125] Cloud users are also express to the control and management of their applications, information and services.[126] This includes information caps, which are placed on cloud users by the deject vendor allocating a certain corporeality of bandwidth for each customer and are often shared among other cloud users.[126]
Privacy and confidentiality are big concerns in some activities. For instance, sworn translators working under the stipulations of an NDA, might face problems regarding sensitive data that are not encrypted.[127] Due to the use of the internet, confidential information such as employee data and user data can be easily available to 3rd-party organisations and people in Cloud Calculating.[128]
Cloud computing has some limitations for smaller business organization operations, peculiarly regarding security and downtime. Technical outages are inevitable and occur sometimes when cloud service providers (CSPs) go overwhelmed in the process of serving their clients. This may result in temporary business suspension. Since this technology'south systems rely on the Internet, an individual cannot access their applications, server, or information from the deject during an outage.[129]
Emerging trends [edit]
| | This department needs expansion. You tin can assistance past adding to it. (September 2021) |
Deject computing is nonetheless a subject of research.[130] A driving factor in the evolution of deject computing has been chief technology officers seeking to minimize chance of internal outages and mitigate the complication of housing network and calculating hardware in-house.[131] They are also looking to share data to workers located in diverse areas in virtually and real-fourth dimension, to enable teams to piece of work seamlessly, no matter where they are located. Since the global pandemic of 2020, cloud technology jumped ahead in popularity due to the level of security of data and the flexibility of working options for all employees, notably remote workers. For example, Zoom grew over 160% in 2020 alone.[132]
Digital forensics in the deject [edit]
The issue of conveying out investigations where the cloud storage devices cannot be physically accessed has generated a number of changes to the fashion that digital evidence is located and collected.[133] New process models have been developed to formalize collection.[134]
In some scenarios existing digital forensics tools can be employed to admission cloud storage as networked drives (although this is a tiresome process generating a large amount of internet traffic).[ citation needed ]
An alternative approach is to deploy a tool that processes in the cloud itself.[135]
For organizations using Office 365 with an 'E5' subscription, there is the choice to use Microsoft's congenital-in e-discovery resources, although these practise non provide all the functionality that is typically required for a forensic process.[136]
See besides [edit]
- Block-level storage
- Category:Cloud computing providers
- Category:Deject platforms
- Communication protocol
- Communications system
- Cloud collaboration
- Cloud native computing
- Deject computing security
- Deject computing comparing
- Cloud management
- Cloud enquiry
- Deject robotics
- Cloud gaming
- Cloud storage
- Cloudlet
- Computer cluster
- Cooperative storage deject
- Dew computing
- Data cluster
- Directory
- Distributed data store
- Distributed database
- Distributed computing
- Distributed networking
- Decentralized computing
- Edge calculating
- Edge device
- eScience
- File system
- Clustered file organisation
- Distributed file organization
- Distributed file organization for deject
- Fog calculating
- Fog robotics
- Green computing (environmentally sustainable computing)
- Grid computing
- In-retentivity database
- In-memory processing
- Cyberspace of things
- Microservices
- Mobile deject calculating
- Mobile edge computing
- Peer-to-peer
- Personal deject
- Robot as a service
- Equally a service
- Service-oriented architecture
- Fourth dimension-sharing
- Ubiquitous computing
- VDI
- Virtual individual cloud
- Spider web calculating
References [edit]
- ^ Ray, Partha Pratim (2018). "An Introduction to Dew Calculating: Definition, Concept and Implications - IEEE Journals & Mag". IEEE Access. 6: 723–737. doi:10.1109/ACCESS.2017.2775042. S2CID 3324933.
- ^ Montazerolghaem, Ahmadreza; Yaghmaee, Mohammad Hossein; Leon-Garcia, Alberto (September 2020). "Green Cloud Multimedia Networking: NFV/SDN Based Energy-Efficient Resource Allotment". IEEE Transactions on Green Communications and Networking. 4 (3): 873–889. doi:10.1109/TGCN.2020.2982821. ISSN 2473-2400. S2CID 216188024.
- ^ "Where's The Rub: Cloud Computing'southward Hidden Costs". Forbes. 2014-02-27. Retrieved 2014-07-14 .
- ^ "What is Cloud Computing?". Amazon Web Services. 2013-03-19. Retrieved 2013-03-20 .
- ^ Baburajan, Rajani (2011-08-24). "The Ascension Cloud Storage Market Opportunity Strengthens Vendors". Information technology.tmcnet.com. Retrieved 2011-12-02 .
- ^ Oestreich, Ken (2010-11-15). "Converged Infrastructure". CTO Forum. Thectoforum.com. Archived from the original on 2012-01-13. Retrieved 2011-12-02 .
- ^ Ted Simpson, Jason Novak, Hands on Virtual Calculating, 2017, ISBN 1337515744, p. 451
- ^ AT&T (1993). "What Is The Cloud?". YouTube. Archived from the original on 2021-10-27. Retrieved 2017-10-26 .
You lot tin can think of our electronic meeting place as the Cloud. PersonaLink was built from the footing up to requite handheld communicators and other devices easy access to a variety of services. [...] Telescript is the revolutionary software engineering that makes intelligent assist possible. Invented past General Magic, AT&T is the first company to harness Telescript, and bring its benefits to people everywhere. [...] Very before long, anyone with a computer, a personal communicator, or television will be able to use intelligent assist in the Cloud. And our new meeting identify is open, and then that anyone, whether private, entrepreneur, or a multinational company, will exist able to offer information, appurtenances, and services.
- ^ Steven Levy (Apr 1994). "Bill and Andy's First-class Gamble 2". Wired.
- ^ White, J.East. "Network Specifications for Remote Task Entry and Remote Job Output Retrieval at UCSB". tools.ietf.org . Retrieved 2016-03-21 .
- ^ "July, 1993 meeting written report from the IP over ATM working group of the IETF". CH: Switch. Archived from the original on 2012-07-10. Retrieved 2010-08-22 .
- ^ Corbató, Fernando J. "An Experimental Fourth dimension-Sharing Arrangement". SJCC Proceedings. MIT. Archived from the original on vi September 2009. Retrieved 3 July 2012.
- ^ Levy, Steven (April 1994). "Bill and Andy'due south Splendid Adventure Two". Wired.
- ^ Levy, Steven (2014-05-23). "Tech Time Warp of the Week: Watch AT&T Invent Cloud Computing in 1994". Wired.
AT&T and the film's director, David Hoffman, pulled out the cloud metaphor–something that had long been used among networking and telecom types. [...]
"You can think of our electronic meeting identify as the cloud," says the flick's narrator, [...]
David Hoffman, the man who directed the flick and shaped all that cloud imagery, was a Full general Magic employee. - ^ "Announcing Amazon Rubberband Compute Cloud (Amazon EC2) – beta". 24 August 2006. Retrieved 31 May 2014.
- ^ Qian, Ling; Lou, Zhigou; Du, Yujian; Gou, Leitao. "Cloud Calculating: An Overview". researchgate.net . Retrieved 19 April 2021.
- ^ "Introducing Google App Engine + our new blog". Google Programmer Web log. 2008-04-07. Retrieved 2017-03-07 .
- ^ "App Engine". cloud.google.com . Retrieved 19 April 2021.
- ^ "Nebula Cloud Computing Platform: NASA". Open Regime at NASA. 2012-11-20. Retrieved 2020-11-15 .
- ^ Rochwerger, B.; Breitgand, D.; Levy, Eastward.; Galis, A.; Nagin, Thousand.; Llorente, I. M.; Montero, R.; Wolfsthal, Y.; Elmroth, E.; Caceres, J.; Ben-Yehuda, M.; Emmerich, W.; Galan, F. (2009). "The Reservoir model and architecture for open up federated cloud calculating". IBM Journal of Inquiry and Development. 53 (iv): iv:1–4:xi. doi:10.1147/JRD.2009.5429058.
- ^ Proceed an center on cloud computing, Amy Schurr, Network World, 2008-07-08, citing the Gartner report, "Cloud Computing Confusion Leads to Opportunity". Retrieved 2009-09-11.
- ^ Gartner (2008-08-eighteen). "Gartner Says Worldwide IT Spending on Pace to Surpass Trillion in 2008". Archived from the original on December 4, 2008.
- ^ "Cluster Exploratory (CluE) nsf08560". www.nsf.gov.
- ^ "285 millions d'euros pour Andromède, le cloud souverain français - le Monde Informatique". Archived from the original on 2011-10-23.
- ^ Hicks, Jacqueline. "'Digital colonialism': why some countries desire to take control of their people's data from Large Tech". The Conversation.
- ^ "Orange enterre Cloudwatt, qui fermera ses portes le 31 janvier 2020". www.nextinpact.com. Baronial 30, 2019.
- ^ "Cloudwatt : Vie et mort du premier " cloud souverain " de la French republic". 29 August 2019.
- ^ "Windows Azure General Availability". The Official Microsoft Blog. Microsoft. 2010-02-01. Archived from the original on 2014-05-11. Retrieved 2015-05-03 .
- ^ Milita Datta (August ix, 2016). "Apache CloudStack vs. OpenStack: Which Is the Best?". DZone · Cloud Zone.
- ^ "OpenNebula vs OpenStack". SoftwareInsider. [ dead link ]
- ^ Kostantos, Konstantinos, et al. "Open up-source IaaS fit for purpose: a comparison between OpenNebula and OpenStack." International Periodical of Electronic Business Direction 11.3 (2013)
- ^ L. Albertson, "OpenStack vs. Ganeti", LinuxFest Northwest 2017
- ^ Qevani, Elton, et al. "What can OpenStack adopt from a Ganeti-based open up-source IaaS?." Cloud Computing (CLOUD), 2014 IEEE 7th International Conference on. IEEE, 2014
- ^ Von Laszewski, Gregor, et al. "Comparing of multiple cloud frameworks.", IEEE 5th International Conference on Deject Computing (CLOUD), 2012.
- ^ Diaz, Javier et al. " Abstruse Image Direction and Universal Image Registration for Deject and HPC Infrastructures ", IEEE 5th International Conference on Cloud Computing (Deject), 2012
- ^ "Launch of IBM Smarter Computing". Archived from the original on 20 April 2013. Retrieved i March 2011.
- ^ "Launch of Oracle Deject". The Register . Retrieved 28 Feb 2014.
- ^ "Oracle Cloud, Enterprise-Grade Cloud Solutions: SaaS, PaaS, and IaaS". Retrieved 12 October 2014.
- ^ "Larry Ellison Doesn't Get the Cloud: The Dumbest Idea of 2013". Forbes.com . Retrieved 12 October 2014.
- ^ "Oracle Disrupts Cloud Industry with End-to-End Approach". Forbes.com . Retrieved 12 October 2014.
- ^ "Google Compute Engine is now Generally Available with expanded OS support, transparent maintenance, and lower prices". Google Developers Blog. 2013-12-02. Retrieved 2017-03-07 .
- ^ Vaughan-Nichols, Steven J. "Microsoft developer reveals Linux is at present more used on Azure than Windows Server". ZDNet . Retrieved 2019-07-02 .
- ^ "Announcing Full general Availability of AWS Outposts". Amazon Web Services, Inc.
- ^ a b c HAMDAQA, Mohammad (2012). Cloud Calculating Uncovered: A Research Landscape (PDF). Elsevier Press. pp. 41–85. ISBN978-0-12-396535-6.
- ^ "Distributed Application Architecture" (PDF). Dominicus Microsystem. Retrieved 2009-06-16 .
- ^ Vaquero, Luis M.; Rodero-Merino, Luis; Caceres, Juan; Lindner, Maik (December 2008). "It'south probable that yous've misunderstood 'Cloud Computing' until now". Sigcomm Comput. Commun. Rev. TechPluto. 39 (1): 50–55. doi:x.1145/1496091.1496100. S2CID 207171174.
- ^ Danielson, Krissi (2008-03-26). "Distinguishing Cloud Computing from Utility Calculating". Ebizq.net. Retrieved 2010-08-22 .
- ^ "Recession Is Good For Cloud Computing – Microsoft Agrees". CloudAve. 2009-02-12. Retrieved 2010-08-22 .
- ^ a b c d "Defining 'Cloud Services' and "Cloud Computing"". IDC. 2008-09-23. Archived from the original on 2010-07-22. Retrieved 2010-08-22 .
- ^ "State of the Art | due east-Fiscal projection". www.efiscal.eu.
- ^ Farber, Dan (2008-06-25). "The new geek chic: Data centers". CNET News. Retrieved 2010-08-22 .
- ^ "Jeff Bezos' Risky Bet". Concern Week.
- ^ He, Sijin; Guo, Fifty.; Guo, Y.; Ghanem, M. (June 2012). Improving Resource Utilisation in the Cloud Environment Using Multivariate Probabilistic Models. 2012 2012 IEEE 5th International Briefing on Deject Computing (CLOUD). pp. 574–581. doi:10.1109/Deject.2012.66. ISBN978-i-4673-2892-0. S2CID 15374752.
- ^ He, Qiang, et al. "Formulating Price-Effective Monitoring Strategies for Service-based Systems." (2013): 1–1.
- ^ Rex, Rachael (2008-08-04). "Cloud Computing: Pocket-size Companies Accept Flight". Bloomberg BusinessWeek . Retrieved 2010-08-22 .
- ^ a b Mao, Ming; M. Humphrey (2012). A Functioning Written report on the VM Startup Fourth dimension in the Cloud. Proceedings of 2012 IEEE 5th International Briefing on Deject Computing (Cloud2012). p. 423. doi:10.1109/CLOUD.2012.103. ISBN978-1-4673-2892-0. S2CID 1285357.
- ^ Bruneo, Dario; Distefano, Salvatore; Longo, Francesco; Puliafito, Antonio; Scarpa, Marco (2013). "Workload-Based Software Rejuvenation in Cloud Systems". IEEE Transactions on Computers. 62 (half dozen): 1072–1085. doi:10.1109/TC.2013.30. S2CID 23981532.
- ^ Kuperberg, Michael; Herbst, Nikolas; Kistowski, Joakim Von; Reussner, Ralf (2011). "Defining and Measuring Cloud Elasticity". KIT Software Quality Departement. doi:10.5445/IR/1000023476. Retrieved thirteen August 2011.
- ^ "Economies of Cloud Scale Infrastructure". Deject Slam 2011. Archived from the original on 2021-10-27. Retrieved 13 May 2011.
- ^ He, Sijin; L. Guo; Y. Guo; C. Wu; M. Ghanem; R. Han (March 2012). Elastic Application Container: A Lightweight Approach for Cloud Resource Provisioning. 2012 IEEE 26th International Briefing on Avant-garde Information Networking and Applications (AINA). pp. 15–22. doi:10.1109/AINA.2012.74. ISBN978-1-4673-0714-vii. S2CID 4863927.
- ^ Marston, Sean; Li, Zhi; Bandyopadhyay, Subhajyoti; Zhang, Juheng; Ghalsasi, Anand (2011-04-01). "Cloud calculating – The business organisation perspective". Decision Support Systems. 51 (1): 176–189. doi:10.1016/j.dss.2010.12.006.
- ^ Why Cloud computing scalability matters for business growth, Symphony Solutions, 2021
- ^ Nouri, Seyed; Han, Li; Srikumar, Venugopal; Wenxia, Guo; MingYun, He; Wenhong, Tian (2019). "Autonomic decentralized elasticity based on a reinforcement learning controller for cloud applications". Time to come Generation Estimator Systems. 94: 765–780. doi:10.1016/j.future.2018.11.049. S2CID 59284268.
- ^ Mills, Elinor (2009-01-27). "Deject calculating security forecast: Clear skies". CNET News. Retrieved 2019-09-19 .
- ^ a b c d east f g h i Peter Mell; Timothy Grance (September 2011). The NIST Definition of Cloud Computing (Technical report). National Institute of Standards and Engineering science: U.S. Department of Commerce. doi:10.6028/NIST.SP.800-145. Special publication 800-145.
- ^ Duan, Yucong; Fu, Guohua; Zhou, Nianjun; Sunday, Xiaobing; Narendra, Nanjangud; Hu, Bo (2015). "Everything as a Service (XaaS) on the Cloud: Origins, Current and Future Trends". 2015 IEEE 8th International Conference on Cloud Computing. IEEE. pp. 621–628. doi:ten.1109/Deject.2015.88. ISBN978-1-4673-7287-nine. S2CID 8201466.
- ^ Amies, Alex; Sluiman, Damage; Tong, Qiang Guo; Liu, Guo Ning (July 2012). "Infrastructure as a Service Cloud Concepts". Developing and Hosting Applications on the Deject. IBM Press. ISBN978-0-13-306684-5.
- ^ Boniface, M.; et al. (2010). Platform-as-a-Service Compages for Real-Time Quality of Service Direction in Clouds. 5th International Briefing on Internet and Web Applications and Services (ICIW). Barcelona, Spain: IEEE. pp. 155–160. doi:10.1109/ICIW.2010.91.
- ^ "Integration Platform equally a Service (iPaaS)". Gartner IT Glossary. Gartner.
- ^ Gartner; Massimo Pezzini; Paolo Malinverno; Eric Thoo. "Gartner Reference Model for Integration PaaS". Retrieved 16 January 2013.
- ^ Loraine Lawson (3 April 2015). "It Business organisation Edge". Retrieved 6 July 2015.
- ^ Enterprise CIO Forum; Gabriel Lowy. "The Value of Data Platform-every bit-a-Service (dPaaS)". Archived from the original on 19 Apr 2015. Retrieved half dozen July 2015.
- ^ "Definition of: SaaS". PC Magazine Encyclopedia. Ziff Davis. Retrieved 14 May 2014.
- ^ Hamdaqa, Mohammad. A Reference Model for Developing Cloud Applications (PDF).
- ^ Chou, Timothy. Introduction to Cloud Computing: Business & Applied science.
- ^ "HVD: the cloud's silver lining" (PDF). Intrinsic Technology. Archived from the original (PDF) on two Oct 2012. Retrieved 30 Baronial 2012.
- ^ Sunday, Yunchuan; Zhang, Junsheng; Xiong, Yongping; Zhu, Guangyu (2014-07-01). "Data Security and Privacy in Cloud Computing". International Periodical of Distributed Sensor Networks. ten (vii): 190903. doi:10.1155/2014/190903. ISSN 1550-1477. S2CID 13213544.
- ^ Carney, Michael (2013-06-24). "AnyPresence partners with Heroku to beef up its enterprise mBaaS offering". PandoDaily . Retrieved 24 June 2013.
- ^ Alex Williams (eleven Oct 2012). "Kii Cloud Opens Doors For Mobile Developer Platform With 25 1000000 End Users". TechCrunch . Retrieved sixteen October 2012.
- ^ Aaron Tan (thirty September 2012). "FatFractal ups the ante in backend-as-a-service market". Techgoondu.com . Retrieved 16 October 2012.
- ^ Dan Rowinski (9 November 2011). "Mobile Backend As A Service Parse Raises $5.5 Meg in Serial A Funding". ReadWrite . Retrieved 23 Oct 2012.
- ^ Pankaj Mishra (seven January 2014). "MobStac Raises $2 Million in Serial B To Help Brands Leverage Mobile Commerce". TechCrunch . Retrieved 22 May 2014.
- ^ "built.io Is Building an Enterprise MBaas Platform for IoT". programmableweb. 2014-03-03. Retrieved 3 March 2014.
- ^ a b Miller, Ron (24 Nov 2015). "AWS Lambda Makes Serverless Applications A Reality". TechCrunch . Retrieved 10 July 2016.
- ^ "bliki: Serverless". martinfowler.com . Retrieved 2018-05-04 .
- ^ Sbarski, Peter (2017-05-04). Serverless Architectures on AWS: With examples using AWS Lambda (1st ed.). Manning Publications. ISBN9781617293825.
- ^ "Cocky-Run Individual Cloud Computing Solution – GovConnection". govconnection.com. 2014. Retrieved Apr 15, 2014.
- ^ "Individual Clouds Accept Shape – Services – Business concern services – Informationweek". 2012-09-09. Archived from the original on 2012-09-09.
- ^ Haff, Gordon (2009-01-27). "Just don't call them private clouds". CNET News. Retrieved 2010-08-22 .
- ^ "There's No Such Thing Equally A Individual Cloud – Deject-computing -". 2013-01-26. Archived from the original on 2013-01-26.
- ^ Rouse, Margaret. "What is public deject?". Definition from Whatis.com. Retrieved 12 October 2014.
- ^ "FastConnect | Oracle Cloud Infrastructure". cloud.oracle.com . Retrieved 2017-eleven-fifteen .
- ^ Schmidt, Rainer; Möhring, Michael; Keller, Barbara (2017). "Customer Relationship Direction in a Public Deject environs - Key influencing factors for European enterprises". HICSS. Proceedings of the 50th Hawaii International Conference on System Sciences (2017). doi:ten.24251/HICSS.2017.513. hdl:10125/41673. ISBN9780998133102.
- ^ "What is hybrid deject? - Definition from WhatIs.com". SearchCloudComputing . Retrieved 2019-08-10 .
- ^ Butler, Brandon (2017-x-17). "What is hybrid deject computing? The benefits of mixing private and public cloud services". Network World . Retrieved 2019-08-11 .
- ^ "Mind the Gap: Here Comes Hybrid Cloud – Thomas Bittman". Thomas Bittman. 24 September 2012. Retrieved 22 April 2015.
- ^ "Business concern Intelligence Takes to Cloud for Small Businesses". CIO.com. 2014-06-04. Retrieved 2014-06-04 .
- ^ Désiré Athow (24 Baronial 2014). "Hybrid deject: is it right for your business?". TechRadar . Retrieved 22 April 2015.
- ^ Metzler, Jim; Taylor, Steve. (2010-08-23) "Cloud calculating: Reality vs. fiction", Network World.
- ^ Rouse, Margaret. "Definition: Cloudbursting", May 2011. SearchCloudComputing.com.
- ^ "How Cloudbursting "Rightsizes" the Data Center". 2012-06-22.
- ^ Kaewkasi, Chanwit (three May 2015). "Cross-Platform Hybrid Deject with Docker".
- ^ Qiang, Li (2009). "Adaptive direction of virtualized resources in cloud computing using feedback control". First International Conference on Information Science and Applied science.
- ^ Cunsolo, Vincenzo D.; Distefano, Salvatore; Puliafito, Antonio; Scarpa, Marco (2009). "Volunteer Computing and Desktop Cloud: The Cloud@Dwelling Image". 2009 Eighth IEEE International Symposium on Network Calculating and Applications. pp. 134–139. doi:10.1109/NCA.2009.41. S2CID 15848602.
- ^ Rouse, Margaret. "What is a multi-deject strategy". SearchCloudApplications. Retrieved 3 July 2014.
- ^ Male monarch, Rachel. "Pivotal'southward head of products: We're moving to a multi-cloud world". ZDnet . Retrieved 3 July 2014.
- ^ Multcloud manage multiple deject accounts. Retrieved on 06 August 2014
- ^ Gall, Richard (2018-05-16). "Polycloud: a improve alternative to cloud agnosticism". Packt Hub . Retrieved 2019-11-eleven .
- ^ Roh, Lucas (31 Baronial 2016). "Is the Deject Finally Ready for Big Data?". dataconomy.com . Retrieved 29 January 2018.
- ^ Yang, C.; Huang, Q.; Li, Z.; Liu, K.; Hu, F. (2017). "Big Data and deject computing: innovation opportunities and challenges". International Journal of Digital Earth. 10 (1): 13–53. Bibcode:2017IJDE...10...13Y. doi:10.1080/17538947.2016.1239771. S2CID 8053067.
- ^ Netto, 1000.; Calheiros, R.; Rodrigues, E.; Cunha, R.; Buyya, R. (2018). "HPC Cloud for Scientific and Business Applications: Taxonomy, Vision, and Enquiry Challenges". ACM Computing Surveys. 51 (1): viii:i–8:29. arXiv:1710.08731. doi:ten.1145/3150224. S2CID 3604131.
- ^ Eadline, Douglas. "Moving HPC to the Deject". Admin Mag. Admin Magazine. Retrieved 30 March 2019.
- ^ "Penguin Computing On Need (POD)". Retrieved 23 January 2018.
- ^ Niccolai, James (11 August 2009). "Penguin Puts High-operation Computing in the Cloud". PCWorld. IDG Consumer & SMB. Retrieved half-dozen June 2016.
- ^ "HPC in AWS". Retrieved 23 Jan 2018.
- ^ "Building GrepTheWeb in the Cloud, Office 1: Cloud Architectures". Developer.amazonwebservices.com. Archived from the original on 5 May 2009. Retrieved 22 August 2010.
- ^ a b c Ryan, Marker D. "Cloud Computing Privacy Concerns on Our Doorstep". cacm.acm.org.
- ^ Haghighat, Mohammad; Zonouz, Saman; Abdel-Mottaleb, Mohamed (2015). "CloudID: Trustworthy cloud-based and cross-enterprise biometric identification". Skilful Systems with Applications. 42 (21): 7905–7916. doi:10.1016/j.eswa.2015.06.025.
- ^ Indu, I.; Anand, P.1000. Rubesh; Bhaskar, Vidhyacharan (August ane, 2018). "Identity and access direction in cloud environment: Mechanisms and challenges". Technology Science and Engineering. 21 (4): 574–588. doi:10.1016/j.jestch.2018.05.010 – via www.sciencedirect.com.
- ^ a b "Google Drive, Dropbox, Box and iCloud Reach the Top v Cloud Storage Security Breaches List". psg.hitachi-solutions.com. Archived from the original on 2015-xi-23. Retrieved 2015-11-22 .
- ^ Maltais, Michelle (26 April 2012). "Who owns your stuff in the cloud?". Los Angeles Times . Retrieved 2012-12-fourteen .
- ^ "Security of virtualization, cloud computing divides IT and security pros". Network Globe. 2010-02-22. Retrieved 2010-08-22 .
- ^ "The Bumpy Route to Private Clouds". 2010-12-twenty. Retrieved 8 October 2014.
- ^ "Should Companies Practice Nigh of Their Computing in the Deject? (Part 1) – Schneier on Security". www.schneier.com . Retrieved 2016-02-28 .
- ^ "Disadvantages of Deject Calculating (Part 1) – Limited control and flexibility". www.cloudacademy.com . Retrieved 2016-11-03 .
- ^ a b "The existent limits of deject computing". www.itworld.com. 2012-05-xiv. Retrieved 2016-11-03 .
- ^ Karra, Maria. "Cloud solutions for translation, yes or no?". IAPTI.org . Retrieved xvi February 2021.
- ^ Pradhan, Sayam (2021). "Cloud Computing". Transitioning from Traditional Data Centers to Cloud Computing: Pros and Cons (ane ed.). Bharat. p. xiv. ISBN9798528758633.
- ^ Seltzer, Larry. "Your infrastructure'southward in the cloud and the Internet goes down. At present, what?". ZDNet . Retrieved 2020-06-01 .
- ^ Smith, David Mitchell. "Hype Wheel for Cloud Computing, 2013". Gartner. Retrieved 3 July 2014.
- ^ "The evolution of Cloud Calculating". Archived from the original on 29 March 2017. Retrieved 22 April 2015.
- ^ "Remote work helps Zoom abound 169% in one yr, posting $328.2M in Q1 acquirement". TechCrunch . Retrieved 2021-04-27 .
- ^ Ruan, Keyun; Carthy, Joe; Kechadi, Tahar; Crosbie, Marker (2011-01-01). Cloud forensics: An overview.
- ^ R., Adams (2013). The emergence of cloud storage and the demand for a new digital forensic process model. researchrepository.murdoch.edu.au. ISBN9781466626621 . Retrieved 2018-03-xviii .
- ^ Richard, Adams; Graham, Mann; Valerie, Hobbs (2017). "ISEEK, a tool for high speed, concurrent, distributed forensic data acquisition". Research Online. doi:ten.4225/75/5a838d3b1d27f.
- ^ "Office 365 Advanced eDiscovery". Retrieved 2018-03-18 .
Further reading [edit]
- Millard, Christopher (2013). Deject Computing Constabulary. Oxford Academy Press. ISBN978-0-19-967168-7.
- Weisser, Alexander (2020). International Taxation of Cloud Calculating. Editions Juridiques Libres, ISBN 978-2-88954-030-3.
- Singh, Jatinder; Powles, Julia; Pasquier, Thomas; Bacon, Jean (July 2015). "Data Period Management and Compliance in Cloud Calculating". IEEE Cloud Computing. 2 (four): 24–32. doi:10.1109/MCC.2015.69. S2CID 9812531.
- Armbrust, Michael; Stoica, Ion; Zaharia, Matei; Flim-flam, Armando; Griffith, Rean; Joseph, Anthony D.; Katz, Randy; Konwinski, Andy; Lee, Gunho; Patterson, David; Rabkin, Ariel (1 April 2010). "A view of cloud calculating". Communications of the ACM. 53 (four): 50. doi:10.1145/1721654.1721672. S2CID 1673644.
- Hu, Tung-Hui (2015). A Prehistory of the Cloud. MIT Press. ISBN978-0-262-02951-3.
- Mell, P. (2011, September 31). The NIST Definition of Cloud Computing. Retrieved Nov 1, 2015, from National Plant of Standards and Technology website
External links [edit]
-
 Media related to Cloud computing at Wikimedia Commons
Media related to Cloud computing at Wikimedia Commons
Gmail Is An Example Fo What Type Of Cloud Computing Service Model?,
Source: https://en.wikipedia.org/wiki/Cloud_computing
Posted by: jaynesdiouse.blogspot.com


0 Response to "Gmail Is An Example Fo What Type Of Cloud Computing Service Model?"
Post a Comment